Information security and data privacy have merged into a new single discipline called data protection. This article discusses developing a data protection program to advance regulatory and contractual compliance.
In Part 2 of this series I discussed the role of data discovery and classification in meeting the many data protection requirements that have been imposed by new laws and regulations. In part 3, I will show how a larger data classification program will help you advance compliance with the many regulations and requirements your company likely faces.
Developing a Data Classification Program
How are the rules that govern sensitive data developed? They derive from a consensus of the organization’s data protection steering committee, a collection of stakeholders (IT/IT Security, Legal, Compliance, HR, and others) that you’ll likely be a member of. The rules are listed in a data classification matrix. A matrix (or schema), such as the one shown below, forms the core of a data classification system. It matches broad categories of data (e.g., Proprietary and Sensitive [C-3], Restricted [C-4], etc.) with approved, mandated controls that are to be used globally by the organization.
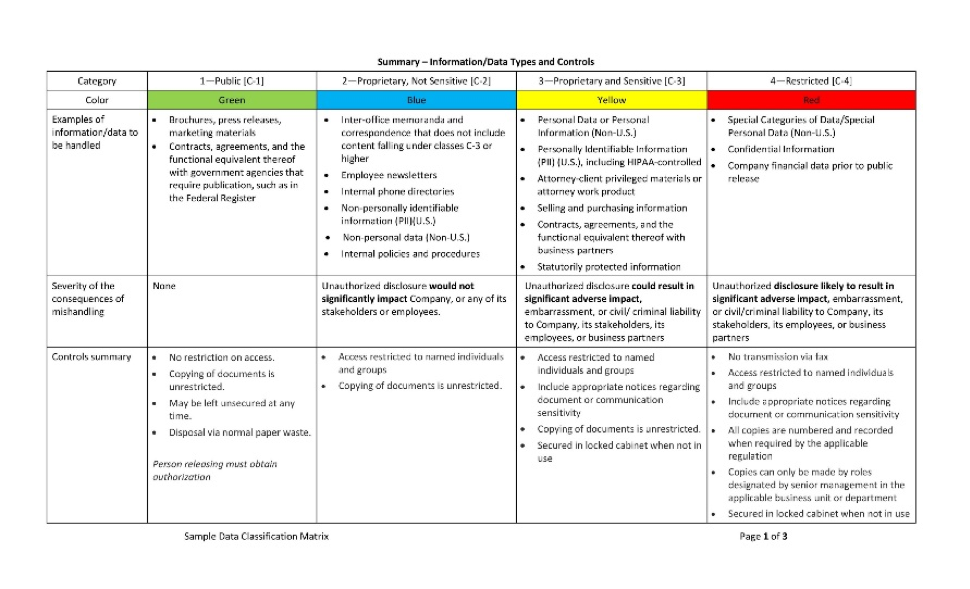
Here, personal data/personal information is categorized as Proprietary and Sensitive [C-3]. Copying of documents containing it is restricted to named individuals, among other controls. The definitions of personal information cited in the GDPR, CCPA, and NYS Part 500 all fall within this category. As such, you would likely add these labels to provide even more granular control of the information. A data classification policy is “wrapped around” the matrix, and is complemented with procedures, plans (e.g., breach notification), and standards. Collectively, these make up the organization’s data protection system. The addition of a data protection steering committee plus commitment from the organization’s leadership creates a data protection program.
Incorporating Policies, Procedures, Plans, and Standards into Data Protection
Polices are an expression of the will of an organization’s leadership, channeled through the steering committee. For example:
“It is the policy of Company to protect information under our control in a consistent, defensible manner that meets our legal, contractual, and ethical requirements.”
From there, the steering committee (or a sub-committee) develops a complete set of subsidiary policies, one of which will be a data classification policy:
- “We classify data according to the potential for harm if control of that data is lost and then match classifications with appropriate controls.”
Examples of other policies include:
- “We only collect personal information that we know we will be using, in accordance with the principle of data minimization.”
- “We design products and systems so that if they fail, they fail into a safe, secure state. This is consistent with the principle of data protection by design and by default.”
- “We endeavor to encrypt data in transit and at rest in a manner that is consistent with generally accepted encryption standards.”
Procedures offer practical, approved means to put policies in effect. For data classification, one procedure might be:
- “All documents will list all relevant classification labels in the document footer.”
Procedures for other policies could be the following:
- “When a request for deletion based on the CCPA is received, check the exceptions list below before proceeding and notify Legal if any of them are likely applicable.”
- “When data that is classified as [C-3] or higher is destroyed, use DoD 5220.22-M as the erasure standard.”
- “When personal data is destroyed, generate and issue a certificate of destruction to the individual requesting its erasure.”
Plans are collections of procedures, with specified roles for team members:
- “Once a breach has been verified by the SOC (security operations center) , business partner, or government agency, use the notification tree to determine who should be contracted and when.”
- “Only designated persons may speak to the news media regarding the event and all communications must be pre-approved using the approval list on page 9.”
Standards are industry-accepted best practices that have been made mandatory by law, contract, or internal best practices:
- “All encryption software must meet FIPS 140-2.”
- “De-identification of personal information labeled HIPAA shall be based on the standards cited by Department of Health and Human Services.”
- “Breach notification plans must incorporate, at a minimum, the procedures cited in OMB M-17-12.”
In part 4 of this series I will discuss using your data protection program to advance compliance with international laws, standards, and contracts.
Information security and data privacy have merged into a new single discipline called data protection. This article discusses developing a data protection program to advance regulatory and contractual compliance.
See how Spirion can help you meet your compliance obligations with data protection. Download the CCPA whitepaper, How Spirion Advances Compliance with the California Consumer Privacy Act of 2018 (CCPA).

