How to take a data-centric approach to security
Cybercriminals are increasingly undermining business security measures to exploit and even hold data hostage. To meet this threat, organizations need more robust and innovative ways to protect their data. This has led to the creation of security models that eschew the old application-centric security architecture and instead take a data-centric approach to security.
Organizations that can achieve secure, compliant, and seamless access to data will outperform those that don’t. Companies have become progressively more aware of this, and in response, are making a tidal shift in how they spend their cybersecurity dollars. In fact, 71% of companies that planned to increase their cybersecurity budgets planned to prioritize data-centric security measures.
What is a data-centric approach to security?
How data is handled – through applications and hardware — is constantly changing, but the actual data organizations own and manage does not change. It only accumulates. Taking a data-centric approach to security can help organizations protect information by putting the focus back on the data and not just the hardware or software applications that house and manage it.
Many traditional security approaches rely on the purchase of application systems that use proprietary data models that bind an organization’s data to its own code. This makes it extremely difficult to move data between new applications, and requires that the data be re-secured at every new endpoint. Every time data must be resecured, it introduces another potential entrypoint for malicious actors.
By moving to a data-centric model, security will focus on the data that needs to be protected as opposed to where that data is housed. This approach ensures that data is protected throughout its existence and not just its life within a single application.
What does a data-centric approach to security look like?
The ideal data–centric security approach consists of the following: discovery, management, protection, and monitoring. This system uses models that automatically protect data from threat actors and fraudulent users, regardless of where that data resides.
Data Discovery
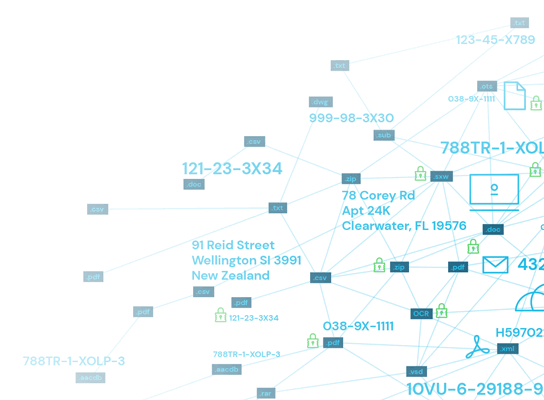
Do you know where your data is? According to a 2015 study from the Ponemon Institute, 64% of companies don’t actually know where their most sensitive data is housed. This is why data discovery is the first step in creating a data-centric security approach. These tools surface the location, context, and volume of data across the entire enterprise – no matter where it’s located. Data can only be secured if the organization knows where it all is.
Access Management
Once the data has been identified, a centralized management system must be put into place to ensure strong and consistent security. Agents are installed to monitor file activity and report back on how it is being used and accessed.
Protection At Rest
An organization’s data is often most vulnerable when it’s being moved among platforms and devices or across networks. This is because in order to be moved it must be decrypted, removing many of its protections. Applying protection at the data level, while it is at rest, ensures that it remains secure even across platforms.
Monitoring
Consistent monitoring, auditing, and reporting is vital to ensure compliance with regulatory bodies. All activities related to data are logged and reported, giving a high level of transparency. Reports can then be generated that show who had access to sensitive data, at what time, on what device, and many other details.
What are the methods involved in securing data at the source?
Taking a deeper look at the more general process above, securing data at the source includes a number of practical tactics that require specialized data management tools. This includes the creation and application of access and policy controls, application of encryption for protection, and finally remediation and monitoring of data via reporting tools.
Data Classification
Establishing data classification protocols is vital to securing data at the source. This allows organizations to separate valuable and sensitive information from less valuable assets. Data is then divided up into the established groups with security controls corresponding to those groups. At Spirion, we use robust classification tools to improve how sensitive data is handled and help enforce governance policies.
Policies and access controls
After data has been classified, the appropriate policies and access controls must be put into place, accounting for business context and other factors. This should be done in tandem with the classification process, as having an understanding of what types of data are available to access is key to creating successful controls.
Data encryption
Encryption protects data by ensuring that it becomes useless to threat actors if breached. Excellent encryption secures data as it moves through applications and devices, and aids in both the maintenance of regulatory compliance and fending off cyberattacks.
There are a number of options for the enterprise deployment of encryption. Often, it is applied in layers that can protect different data types as they are accessed and managed. While the investment in encryption may seem steep, it more than pays for itself. This is because solid end-to-end encryption tools can streamline processes, lower costs, and reduce risks.
Data remediation and monitoring
Finally, when all of the pieces are in place, the data remediation process should begin. Data remediation is the act of cleansing, organizing, and migrating data. This does not simply mean removing data that is no longer needed, but also correcting any inaccurate data, which may involve replacing, modifying, cleansing, or deleting some types of data. At Spirion, we have proprietary tools to complete this activity.
What are the benefits of a data-centric approach to security?
Taking a data-centric approach to security can assist organizations in upholding regulatory compliance while removing growth barriers. One recent study found that most organizations struggle to balance managing increasing cybersecurity threats without sacrificing the speed of business. The growing remote-work trend has only accelerated these concerns, as it has opened new threat opportunities for cybercriminals.
As data volume accelerates and workers become increasingly dispersed around the globe, intrusions via perimeter breaches are also likely to continue its upward trend. Organizations will need to implement more endpoint security, data controls, and access management. This is where a data-centric approach to security can really benefit an organization.
How Spirion can help you adopt a data-centric security approach
Implementing a data-centric security model can improve transparency while providing streamlined and consistent protection of data. This can minimize security risks that pose substantial threats to businesses today in the form of financial, reputational, and regulatory breaches.
Spirion’s suite of data-centric security solutions can streamline and simplify your organization’s approach to risk management. Contact Spirion to discover more about the application of a data-centric security approach for your organization.
