
BY SPIRION
October 29, 2025
In modern, complex security and compliance environments, not all sensitive information is created equally. Government and defense contractors and suppliers, research institutions, and private enterprises often handle multiple categories of sensitive data, each with its own governance rules, handling requirements, and consequences for mishandling.
A common point of confusion is understanding where Controlled Unclassified Information (CUI) fits alongside classified information and other forms of sensitive data like Personally Identifiable Information (PII) or Payment Card Information (PCI).
This article breaks down the distinctions, why they matter, and how organizations can meet compliance regulations and legal obligations while ensuring comprehensive protection of all sensitive data types.
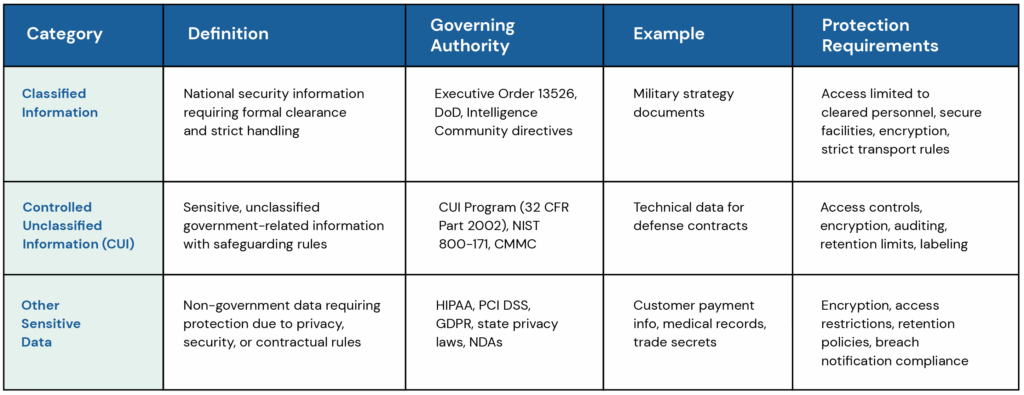
Classified Information
Definition: Information owned by, produced for, or under the control of the U.S. Government that requires protection for national security reasons.
Levels: Top Secret, Secret, Confidential — each with specific clearance and handling rules.
Governance: Classified under Executive Order 13526 and related policies.
Examples: Military operational plans and intelligence reports.
Controlled Unclassified Information (CUI)
Definition: Information the U.S. Government creates or possesses, or that an entity creates for or on behalf of the Government, that requires safeguarding or dissemination controls but is not classified. It encompasses a wide range of information related to defense, intelligence and critical infrastructure.
Purpose: Protect sensitive but unclassified data critical to government interests, contracts, or operations.
Governance: Managed under the CUI Program (32 CFR Part 2002) and tied to standards like NIST SP 800-171 and CMMC for Defense contractors.
Examples: Technical drawings for a defense component and export-controlled research data.
Other Sensitive Data Types
Definition: Information that, while not regulated under classification or CUI frameworks, still requires protection to comply with industry, privacy, or contractual obligations.
Common Sensitive Data Types:
- Personally Identifiable Information (PII)
Examples: Employee and customer information, including Names, SSNs, addresses.
Governance: Various regional privacy laws, including the EU’s GDPR, California CCPA, Australia’s POLA Act, etc.
- Protected Health Information (PHI)
Examples: Patient information and medical records
Governance: Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Information (PCI)
Examples: Primary Account Number (PAN) and Cardholder Name
Governance: Payment Card Industry Data Security Standard (PCI DSS)
- Intellectual Property (IP)
Examples: Proprietary formulas and technology
Governance: Non-Disclosure Acts (NDA), company policies and export-control regulations
- Confidential Business Data
Examples: Board and M&A documents
Governance: Non-Disclosure Acts (NDA) and company policies
At-a-Glance Comparison Chart
Why the Distinction Between Data Types Matters
Compliance: Different regulations and contractual clauses apply. Failing to meet one does not excuse gaps in another.
Risk Management: A breach of any category can lead to serious legal and financial consequences, and reputational damage.
Technology Needs: Effective data security requires the ability to accurately discover, classify, and secure all types of sensitive data in your care.
Finding and Protecting All Data Types
Many organizations have solutions in place for one category of sensitive data, such as encrypting classified data and CUI, but lack visibility into unclassified yet sensitive information like PII. The reality is that all sensitive data must be safeguarded appropriately. What makes this a challenge is the fact that sensitive data is spread out everywhere — from cloud platforms to on-premises tools to employee laptops.
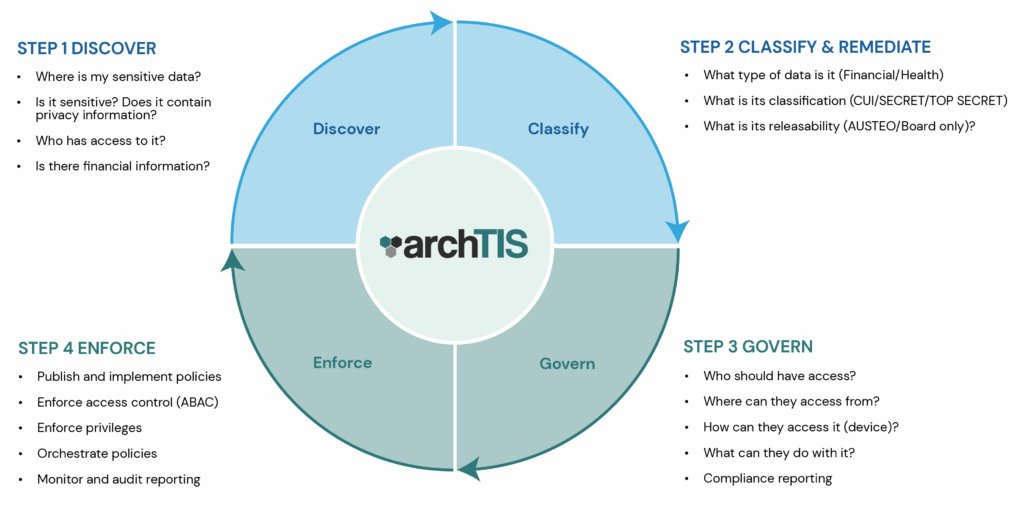
The protection of sensitive data can be summarized in four critical steps: discovery, classification, governance and enforcement.
- Discovery to understand the location and sensitivity level of all business information,
- Classification to categorize data appropriately,
- Governance to define policies around who can access data and under what conditions, and,
- Enforcement to apply all the necessary protective measures according to the sensitivity level.
A robust end-to-end solution for sensitive data management and compliance should include the following capabilities:
- Comprehensive Discovery: Locating sensitive data across all endpoints, servers, cloud services, and collaboration tools and defining who has access to it.
- Granular Classification: Applying the right labels and handling rules for each category of data.
- Automated Remediation: Ensuring sensitive data is stored, shared, or deleted according to its requirements.
- Access Controls: Enforcing policies on who can access sensitive data and under what conditions according to regulatory requirements for each category of data.
- Encryption: Encrypting information based on its classification to restrict access and meet compliance-specific requirements.
- Auditing & Reporting: Log and track sensitive data access, user activities and actions such as producing, editing or deleting data, and general access for compliance auditing and reporting.
Achieving Effective Data Governance and Security
Data security and integrity are vital to any organization’s protection of its most critical asset—data. Data discovery, classification, governance and enforcement measures are critical to preventing sensitive data loss and exposure.
Understanding the differences between sensitive data types isn’t just about compliance—it’s essential to building a robust governance program that truly protects your organization’s most critical information and your relationship with government and enterprise customers. In doing so, you safeguard your reputation and bottom line.
