
BY SPIRION
August 4, 2025
Amid constant cyber threats and rapid digital transformation, it might seem surprising that one of the most powerful tools in the federal government’s arsenal for fighting cybersecurity noncompliance was born during the Civil War. But as whistleblower attorney Julie Bracker, partner, Bracker & Marcus LLC explained during our recent “Hidden Data. Thriving Threats.” webinar, the False Claims Act (FCA), also known as “Lincoln’s Law”, has never been more relevant.
Born Out of Battlefield Deception
The FCA was created in 1863 as a response to wartime fraud. Contractors were sending mules instead of horses, uniforms made from material barely thicker than coffee filters, and barrels of flour infested with weevils. Because the federal government had no effective communication or inspection systems at the time, it was nearly impossible to catch these bad actors before they vanished with taxpayer money.
So, the government came up with a bold idea: “Set a rogue to catch a rogue.” The law empowered private citizens, whistleblowers, to sue on behalf of the government and share in any financial recovery. This provision, called a qui tam action, remains at the heart of the FCA today.
A Legal Renaissance in the Age of Data
After falling dormant for decades, the FCA came roaring back in the 1980s, spurred by infamous stories of $600 toilet seats and inflated government contracts. Legislative reforms brought new energy and new targets, from military procurement fraud to, eventually, healthcare fraud and data privacy violations.
Since 2010, annual recoveries under the FCA have exceeded $2 billion every year. In 2024 alone, $2.9 billion was recovered across 1,400 cases, the highest volume ever filed. Eighty-three percent of those were initiated by whistleblowers.
Cybersecurity: The Next Frontier of FCA Enforcement
With the Department of Justice’s Civil Cyber-Fraud Initiative (CCFI), cybersecurity is now squarely in the FCA’s crosshairs. The DOJ has made it clear: if you’re a government contractor and you claim to be cyber-compliant but aren’t, that’s a false claim.
The most common pitfall? Signing off on compliance with DFARS 7012 and NIST 800-171 standards without an actual System Security Plan (SSP) or risk assessment. Many organizations unknowingly (or knowingly) skip the foundational step of assessing where their sensitive data lives, and how it’s secured.
“The best time to start was seven years ago. The next best time is now.”
–Julie Bracker, Partner, Bracker & Marcus LLC
“We Haven’t Had a Breach” Is Not a Defense
Many organizations assume that because they haven’t been breached, they’re safe. But as Julie emphasized, there’s no requirement under the FCA to show actual damages. If you misrepresented your security posture to win a federal contract, even if no data was exfiltrated, you’re still liable.
In some cases, the exposure can be massive. FCA penalties currently range from $14,000 to $28,000 or more per false claim. And if you’re billing monthly? That’s 12 separate false claims per year, multiplied by the number of years and contracts.
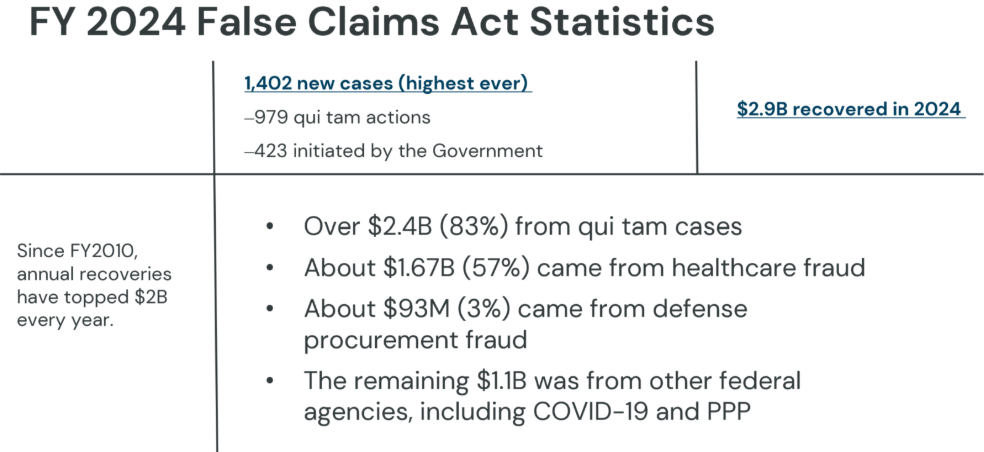
Figure 1: FCA fines continue to top billions every year for those who are out of compliance.
Lessons from the Front Lines: What’s Really at Stake
The risk isn’t theoretical. Bracker shared chilling examples of contractors holding military data on unsupported systems or reporting compliance without moving critical data into secured enclaves. In some cases, the only reason we haven’t seen more damage is luck, not resilience.
She also underscored a key takeaway: trust but verify. Third-party audits, not internal spreadsheets, are essential if you want to prove defensibility and avoid FCA exposure.
The Takeaway for CISOs and Legal Teams
This isn’t just about checkboxes. It’s about integrity, accountability, and the need for an active, data-centric approach to cybersecurity posture. Organizations that work with federal data, directly or indirectly, must:
- Understand their obligations under the Civil Cyber-Fraud Initiative
- Assess where Covered Defense Information (CDI) and other sensitive data resides
- Establish and maintain a realistic, defensible data protection program
- And proactively correct misrepresentations through self-disclosure where needed
Spirion’s Role in Reducing Your Risk
Spirion helps federal contractors and private-sector organizations alike achieve sustainable compliance by delivering unmatched visibility into where your sensitive data lives: structured, unstructured, in the cloud, or on endpoints. With Spirion’s Sensitive Data Platform (SDP) and Spirion Data Watcher, you can:
- Discover and classify CUI and other regulated data
- Audit and monitor access to reduce insider risk
- Apply DSPM controls that reduce the attack surface and prevent false attestations
Final Thought: Start Yesterday
As Bracker put it, “The best time to start was seven years ago. The next best time is now.” If you’re not 100% sure your data security claims are defensible, the FCA, and the next whistleblower, might be closer than you think.
