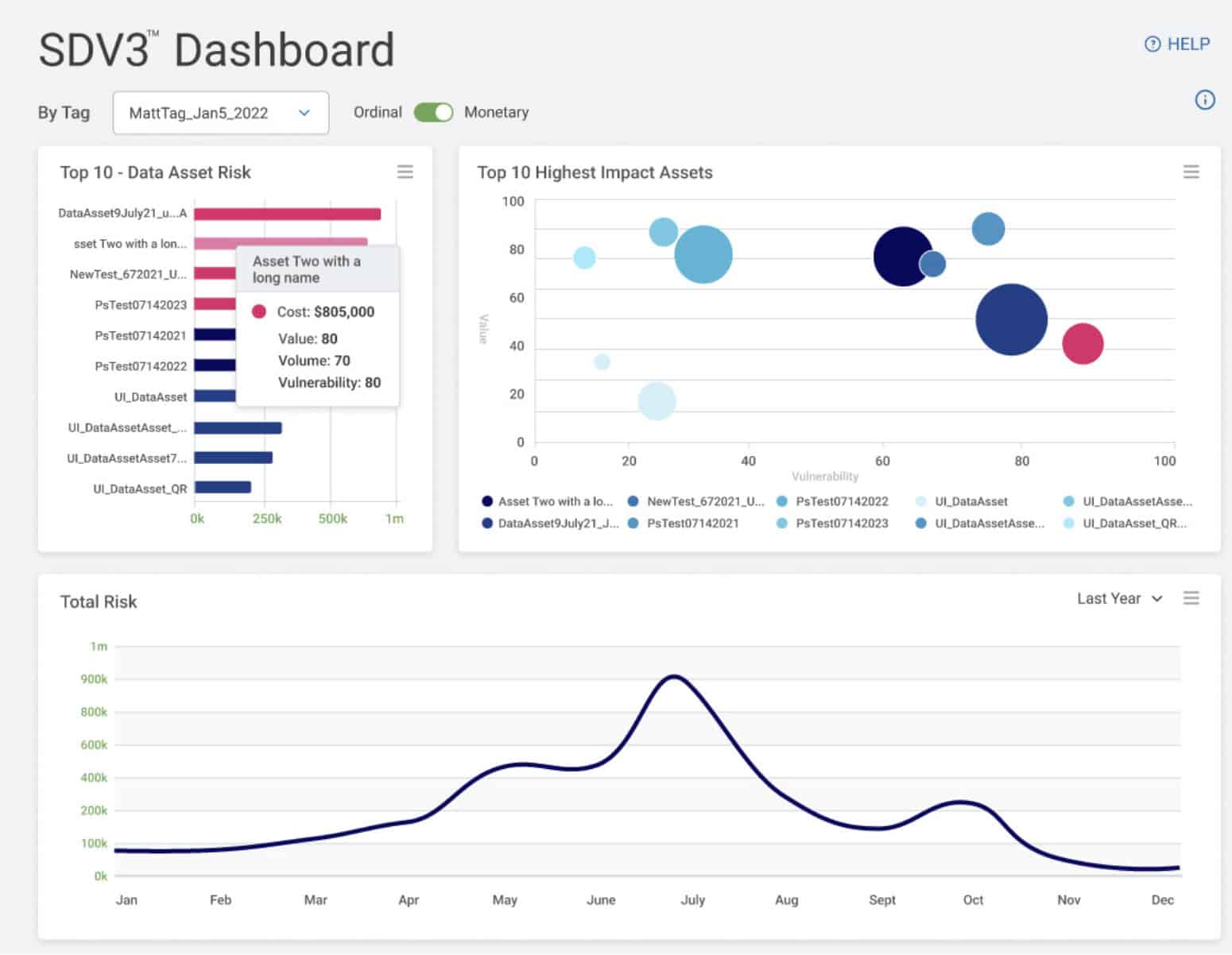
Quantify Data Risks:
Understand data risk setting priorities and managing the riskiest assets for objective decision-making.
Validate Security ROI:
Prove the value of security investments over time with historical trendlines capturing monetary impact.
Drive Data Security Cases:
Support business cases for new data security investments using objective, quantifiable metrics.
Patent-Pending Scoring Algorithm
Value
The relative value that you assign to a data asset, based on a monetary amount or ordinal ranking. SDP’s standard global data type definitions are preloaded with values from the IBM Ponemon “Cost of Data Breach” report which can be customized to your internal breach cost metrics.
Patent-Pending Scoring Algorithm
Volume
The volume of sensitive data in the asset. As you assess your data risks, you can quickly spot opportunities to remove unneeded, ROT (redundant, outdated, or trivial) data to minimize your sensitive data threat surface.
Patent-Pending Scoring Algorithm
Vulnerability
Based on location and overall data posture, how vulnerable is your data to being compromised or misused, either inadvertently or maliciously? For example, sensitive data on a remote worker’s laptop would have a higher vulnerability score than an encrypted dataset behind an enterprise firewall. Each factor can have an equal weighting, or you can change the weightings as desired.
Key Features
Dynamic Risk Metrics:
Quantitative assessment of data risks based on value, volume, and vulnerability for transparent decision-making.
Customizable Value Assignments:
Adjust values based on internal breach cost metrics or use preloaded values from industry reports.
ROT Data Identification:
Spot opportunities to minimize threat surface by quickly identifying redundant, outdated, or trivial data.
Location-Based Vulnerability Scoring:
Evaluate data vulnerability based on location, enhancing precision in risk assessment.
Continuous Trendline Analysis:
Historical trendlines capture the value of security initiatives, showcasing return on investment over time.
Objective Metrics for Business Cases:
Provide quantifiable metrics for compelling business cases supporting new data security investments.
Data Risk Reporting:
Timely and updated risk reports highlight important trends for effective communication with regulators and management.
Variable-Specific Risk Identification:
Identify high-risk areas by data owner, location, or other variables, facilitating targeted risk mitigation efforts.
Check out our Solution Overview
Asset-specific risk metrics to quantify, assess, and prioritize your data security posture
