
BY SPIRION
July 29, 2025
In the modern regulatory minefield, one of the most deceptively complex questions facing legal, privacy, and IT leaders is: What qualifies as sensitive data?
During the webinar, “Hidden Data, Thriving Threats.”, Scott Giordano, Esq., The Ciso Law Firm, attorney and subject matter expert on privacy regulations, walked attendees through the 50-year history of data privacy laws, and how recent regulatory shifts, from GDPR to CCPA and beyond, have redefined sensitivity in personal and corporate contexts.
A Legal Evolution 50 Years in the Making
Scott traces the evolution of privacy legislation starting with the Privacy Act of 1974, plodding along slowly until 2013 when Edward Snowden’s revelations accelerated global regulatory momentum. This turning point gave rise to sweeping frameworks like the GDPR, which in turn inspired CCPA, CPRA, and now a growing list of global privacy laws. Each adds new categories and stricter expectations around what qualifies as sensitive.
Today, it’s no longer just Social Security numbers or healthcare records. It’s geolocation, email, behavioral inferences, and even data pulled from smartphone accelerometers: information that can reveal health conditions, gender, personality traits, and more.
What Makes Data Sensitive Today?
Scott breaks sensitivity into two key buckets:
1. Personally sensitive data
- Biometric, genetic, geolocation, financial, and now neural data (yes, that’s being tracked too)
- Communications like email, postal mail, and text messages
- Inferences made from devices or analytics, including emotional states or behavior
2. Contextually sensitive corporate data
- Controlled Unclassified Information (CUI) in federal contracts
- Event data and log files critical to breach investigations
- Data baked into AI models that can’t be untrained
And with laws like Washington’s My Health, My Data Act and Colorado’s AI-specific regulations going into effect, the legal definition of ‘sensitive’ keeps expanding. For organizations across industries, that means data once thought harmless may now trigger liability or litigation.
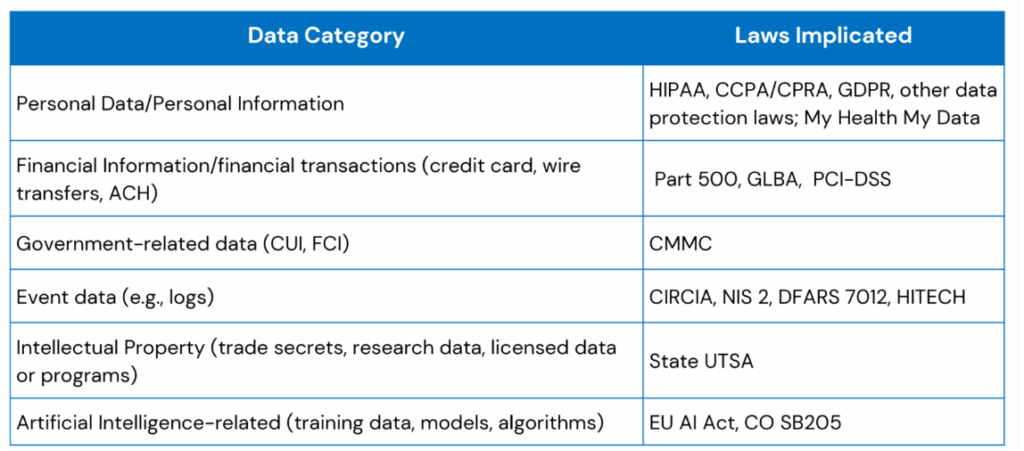
Figure 1: The suite of regulatory laws defining sensitive data continues to expand to include information you may have but didn’t know was protected.
The Solution? A Defensible Data Inventory
If there’s one place to begin addressing your organization’s data risk, Scott says it’s with a data inventory.
“I learn more about my clients through their data inventory than from all other interviews combined. You’ll find data you thought was deleted or didn’t even know existed.”
–Scott Giordano, Esq., Partner & Co-Founder, The CISO Law Firm
A data inventory:
- Acts as a single source of truth across your ecosystem
- Powers all downstream privacy assessments (DPIAs, AI audits, etc.)
- Reveals forgotten systems or risky access pathways
- Helps validate regulatory compliance and breach response
- Reduces the risk of surprise liabilities, audits, or whistleblowers
And in an age where prompt injection attacks, third-party partner exposures, and scope creep in privacy laws are becoming standard, this isn’t just a privacy exercise, it’s a business continuity imperative.
Bottom Line: You Can’t Protect What You Don’t Know You Have
If your organization is still asking, “Where is our sensitive data?” or “What does sensitive really mean?”, you’re already behind.
Watch the full clip to understand how privacy laws are evolving, what regulators expect, and why building a defensible data inventory must be your next move.
