In recent years, a whole host of new laws regulating how sensitive information is collected, used, stored, shared, and disposed of have been enacted. Having a data protection program in place will help companies with compliance and reduce the risk of data breaches.
Data privacy background
The U.S. and European Union took two completely different approaches to data privacy and security. The U.S. opted for industry-specific laws, so rules regulated how personal data could be used in specific sectors, which left the door open for it to be incorrectly used in other contexts. The EU implemented a broader law that applied to all industries, nonprofits, and government agencies, but it unfortunately couldn’t keep up when mobile devices, cloud computing and social media entered the picture. It did, however, lay the groundwork for the General Data Protection Regulation (GDPR) that exists today. In turn, the GDPR influenced new security and privacy measures in the U.S., such as the California Consumer Privacy Act (CCPA), with more states following suit to implement similar regulations.
Data compliance obligations
While the basics of certain regulations can be similar, such as the GDPR and CCPA, providing broad protection of personal data in their respective regions, the actual compliance obligation definitions vary. To be compliant with the GDPR, organizations must:
- Accurately identify all personal data under their control.
- Give data subjects access to their personal data.
- Maintain data security.
- Notify authorities of data breaches.
- Police third-party processing of personal information.
- Keep timely and accurate records of data protection activities.
To be compliant with the CCPA, organizations must:
- Publish their privacy practices.
- Disclose to consumers what personal information has been collected in the preceding 12 months.
- Honor requests for data deletion.
- Enable consumers to direct third parties not to use their personal information.
In addition, organizations conducting cross-border transactions must commit to data protection clauses, which can allow for random audits of the data processor by the data controller and require the data processor to obey the governing law of the data controller’s jurisdiction. These clauses also contain numerous other tasks for both controllers and processors to maintain. For example, controllers often mandate processors comply with ISO 27001, an international data security standard.
A data protection system can offer unique capabilities that advance compliance with these cross-border and similar agreements, particularly the ability to identify and protect sensitive information in accordance with standards such as ISO 27001 and strengthen an organization’s overall data protection program.
Creating a data protection system
Your data protection system is a two-pronged approach that involves:
- Discovery of sensitive information and creation of a data inventory.
- Classifying that information according to the organization’s data protection standards.
Data discovery
Data discovery involves electronically searching an organization’s network and cloud stores for all sensitive data. Once it’s identified, it can be properly classified. Undiscovered data risks going unprotected, which results in noncompliance.
Data classification
Data classification looks at all the data identified during discovery and labels it appropriately based on its level of sensitivity. These labels are indicative of the controls that must be applied and regulations to which the data is subject. They can also address information governance mandates such as how long to keep the data before destroying it. The rules governing these labels should be listed in a data classification matrix, which helps to maintain consistent classification as well.
Data classification matrix
A matrix (or schema), such as the one shown below, forms the core of a data classification system.
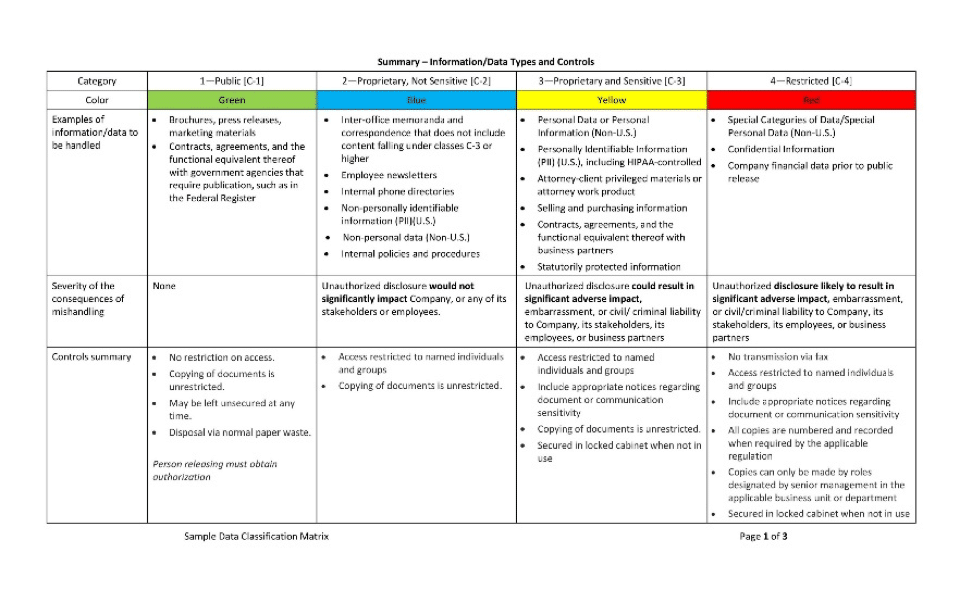
It matches broad categories of data (e.g., Proprietary and Sensitive [C-3], Restricted [C-4], etc.) with approved, mandated controls that are to be used globally by the organization.
A data classification policy revolves around the matrix and is complemented with procedures, plans (such as breach notifications) and standards. Collectively, these make up the organization’s data protection system. The addition of a data protection steering committee, plus commitment from the organization’s leadership, creates a data protection program.
Maintain data privacy obligations with Spirion
Sprion’s Sensitive Data Platform discovers and classifies data with unmatched accuracy. What’s more, as your organization scales up and more data comes into play, Spirion’s platform automates discovery, classification, and remediation, allowing you to remain compliant as you grow. Contact us today to see how Spirion can help you meet your present and future compliance obligations with a fortified data protection program.


