
BY JEREMY FIELDS
May 6, 2024
A ModerNIST Manifesto
The National Institute of Standards and Technology (NIST), an agency founded in 1901, published its Cybersecurity Framework Version 1.0 (CSF 1.0) on February 12, 2014, in response to Executive Order 13636 issued a year prior. Originally scoped around critical infrastructure, it was conceived to be, “a set of [security] standards and best practices to help organizations manage cybersecurity risks.”
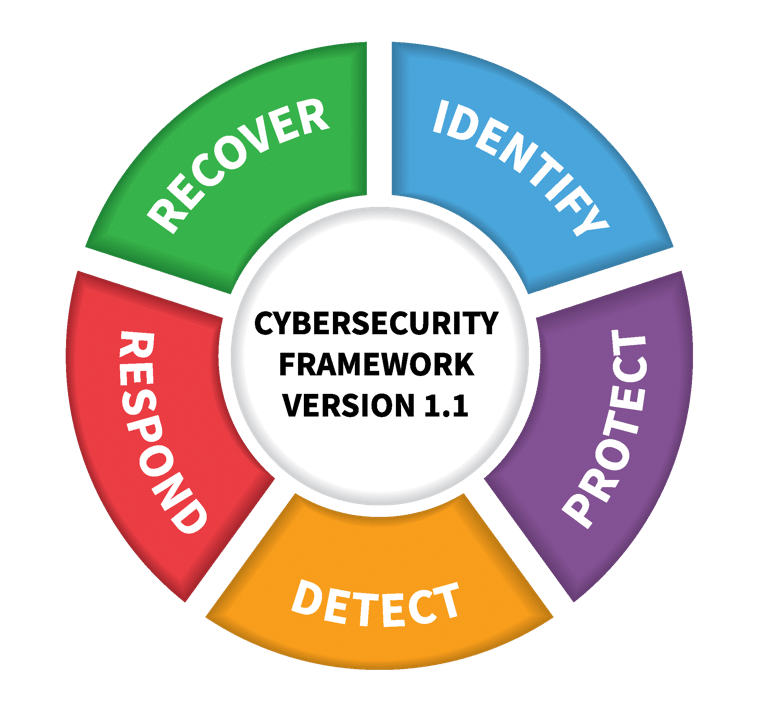
Five core functions have served as foundational activities for the CSF since its debut: Identify, Protect, Detect, Respond, and Recover. The framework then divides each segment into categories and subcategories to lay out benchmarks for success to substantiate the achievement of each primary function.
Credit: N. Hanacek/NIST
Authors of the first Cybersecurity Framework described their effort as a living document intended to complement ongoing risk management and security operations. Its core functions were drafted deliberately for organizations of all sizes across all industries, representing a concurrent and continuous means to the end of closing the inevitable gaps between current and ideal target states of cybersecurity posture.
Hello 2.0
Four years after CSF 1.0 was released, NIST refined its advice by publishing the Cybersecurity Framework Version 1.1 in 2018. This added new categories and subcategories to the existing functions as well as revised content for clarity after soliciting feedback from those who had implemented 1.0.
Earlier this year, on February 26, 2024, the first major revision was announced to better align with the latest National Cybersecurity Strategy issued in March of 2023. The changes realized in CSF 2.0 include emphasizing new problems, reorganizing pivotal concepts, and ensuring that the appropriate resources and references are available to enable adoption.
Governance is the Glue
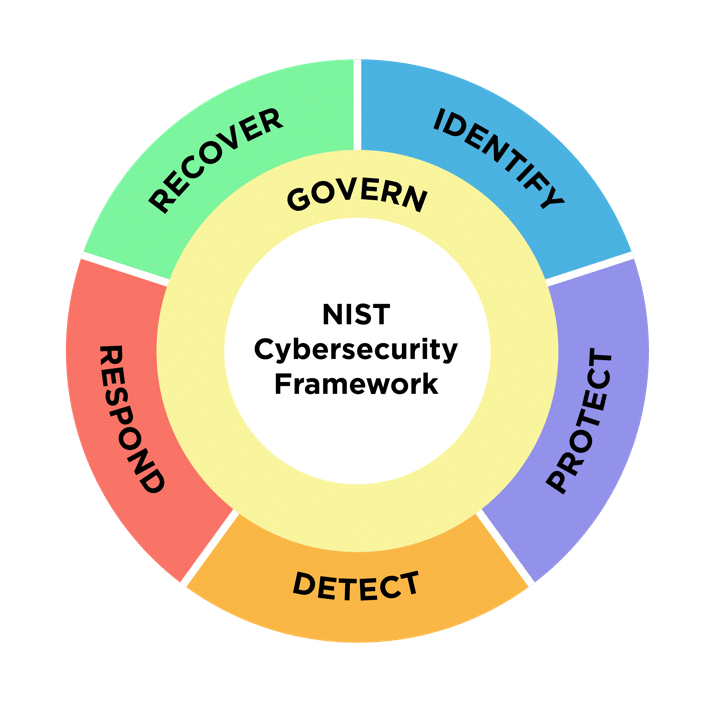
CSF 2.0 introduces a new function, Govern. It strengthens all other functions in the framework, as indicated by its placement within the wheel rather than existing as a standalone segment. Activities related to this function are meant to better guarantee effective outcomes for tasks associated with the remaining CSF core functions.
Credit: N. Hanacek/NIST
Previously a category nested under the Identify function with only 4 subcategories, there are now 6 categories (and 21 subcategories) related to the governance of an organization’s cybersecurity posture:
- Organization Context (GV.OC): ensures clarity of purpose.
- Risk Management Strategy (GV.RM): leads to deliberate policies.
- Roles, Responsibilities, and Authorities (GV.RR): defines accountability.
- Policy (GV.PO): enforces prioritized outcomes.
- Oversight (GV.OV): evaluates necessary adjustments.
- Cybersecurity Supply Chain Risk Management (GV.SC): accounts for indirect risk.
All Infrastructure is Critical
Besides the new, inner Govern ring, the most obvious modification is right on the first page’s “Note to Readers” section, which says:
Before version 2.0, the Cybersecurity Framework was called the “Framework for Improving Critical Infrastructure Cybersecurity.” This title is not used for CSF 2.0.
This shift echoes throughout the document. In expanding beyond the direct goals of the Executive Order that initially prompted its drafting (CSF 1.0), the framework turns out to be universally applicable with only minor adjustments to its language – while still preserving the core message intended for critical infrastructure such as power plants and hospitals.
Key to its newfound declaration of general relevance is the fact that, from the very first release, NIST emphasized how CSF implementations are not envisioned to form a comprehensive checklist of actions that add up to a state of invulnerability. They instead serve as a basis upon which meaningful results can be validated in accordance with whatever standards or regulatory obligations are required by an organization.
Organizing Framework Profiles
Another somewhat semantic shift is the new messaging around using Organizational Profiles to track current and/or target conditions of cybersecurity resilience. Previous CSF versions called these artifacts Framework Profiles and did not offer much in terms of guidance other than accruing a library of referenceable profiles over time. It is worth noting that each profile should be purposely defined to support categorically similar situations, though organizations are encouraged to leverage as many profiles as necessary.
With CSF 2.0, NIST has outlined step-by-step directions to arrange Organizational Profiles. It has additionally introduced the concept of Community Profiles, which are publicly hosted examples of baseline outcomes meant to cover worries shared in common by industries, technologies, or other use cases. To get started, there is a Notional CSF 2.0 Profile Template available and promises of a “build your own pre-populated template” coming soon.
Five Steps to Creating Organizational Profiles:
- Scope the Organizational Profile – what factors will be addressed?
- Gather the needed information – what reference data should be incorporated?
- Create the Organizational Profile – what is the current and target state for each CSF outcome?
- Analyze gaps and create an action plan – what can be improved?
- Implement action plan and update Profile – what can be done to achieve said improvements?
References & Examples & Guides, Oh My
As alluded to in the previous section, NIST has given more attention to what organizations may need to get started on their CSF journey, no matter their size, focus, or technical sophistication. This is made abundantly clear when browsing the CSF 2.0 Resource Center compared to the CSF 1.1 Archive. The latter is not void of helpful information; however, it is clearly a precursor to the content supplementing this latest edition.
Notably, the CSF Quick Start Guide (QSG) materials have been expanded to address 6 topics:
- Creating & Using Organizational Profiles
- A Guide to Creating Community Profiles
- Small Business Quick-Start Guide
- Cybersecurity Supply Chain Resource Management
- Using the CSF Tiers
- Enterprise Risk Management
There is also a new type of documentation collected in the Informative References hub. Most impressive here is the National Online Informative References (OLIR) Program’s Cross-Reference Comparison Report generator, capable of evaluating a source NIST publication – with 8 choices available – and then indicating where sections from a secondary document overlap with the selected source.
CSF 2.0 is included as a source selection and can currently be aligned to 4 references: CSF 1.1, SP 800-221A, SP 800-53 Rev 5.1.1, and SP 800-218.
Supply Chain Security Spotlight
In CSF 1.0 there was only a single mention of supply chain risk in the Identify function. Then, CSF 1.1 expanded supply chain risk management into its own category with 4 subcategories, still specific to Identify.
Now, with CSF 2.0, the topic is a category within Govern, meaning it informs every other function. Its 10 subcategories place intentional emphasis on the necessity to identify, establish, manage, monitor, and improve supply chain risk management, so much so that there is a QSG dedicated to best practices for relevant processes (linked above).
CSF & DSPM: Initial Considerations
Armed with the modernized CSF 2.0, those responsible for Data Security Posture Management (DSPM) should be able to better coordinate their efforts across departments and stakeholders. The cross-functional objectives of the new Govern function give credence to the notion that corporate data is “owned” by the entire business, as opposed to the IT teams tasked with maintaining the infrastructure through which it is accessed.
By explicitly broadening the target audience of the framework, NIST correctly positions CSF recommendations as a frame of reference for any and all organizations operating information and communications technology (ICT)… which is of course every business with a digital footprint. The need to implement data-centric information security policies is an equally universal need as nobody is spared from the financial and reputational damages due to the abuse or misuse of information in their control.
Having the appropriate reference material is another strong theme throughout CSF 2.0. Perhaps most crucial is knowing how to produce Organizational Profiles that apply the framework to various types of security concerns. The next installment of this blog post will contain guidance about Spirion’s CSF 2.0 policy map to secure DSPM, digging into where Sensitive Data Platform (SDP) contributes to the 6 key functions presented in this year’s update.
