BY JEREMY FIELDS
May 13, 2024
Spirion’s CSF 2.0 Policy Map to Secure DSPM
Knowing that the CSF has always suggested a categorical approach when designing Organizational Profiles, a data-centric CSF policy should be at least considered, if not pursued, to augment Data Security Posture Management (DSPM) undertakings. This holds even more true after CSF 2.0’s latest enhancements (see Part 1 for details).
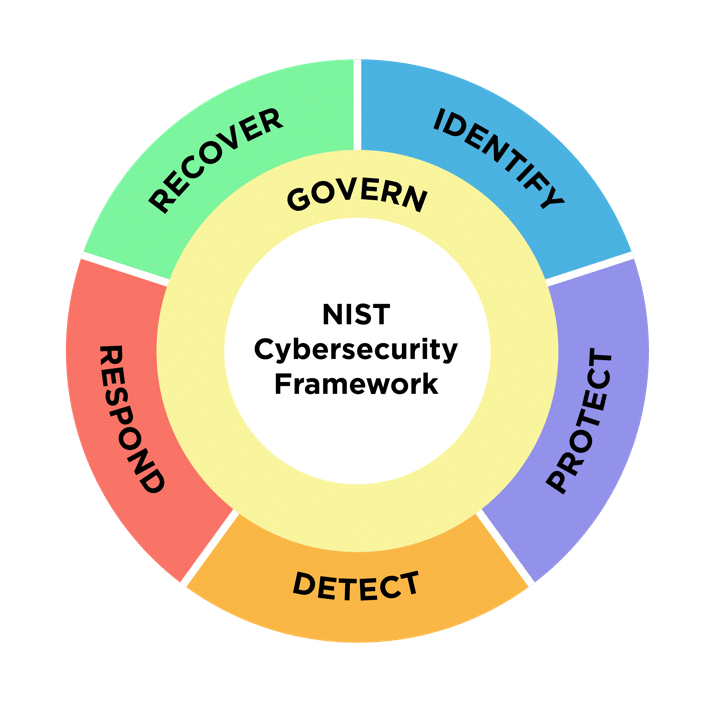
Through the lens of these recommendations, many parallels between CSF 2.0’s functions and DSPM’s best practices become evident.
Spirion provides a comprehensive solution to equip organizations with a foundation for DSPM success. Data discovery, classification, and remediation – Spirion’s principal features – are intrinsically tied to the 6 CSF core functions. In addition, the result notifications, alerts, and reports generated by Spirion contribute to a more complete understanding when it comes to the framework’s more auxiliary activities.
NOTE: While the CSF 2.0 PDF document contains a list of all functions, categories, and subcategories (on pages 16 through 23), there is an interactive version published as the CSF 2.0 Reference Tool.
Govern: Master-ring the 5 Functions
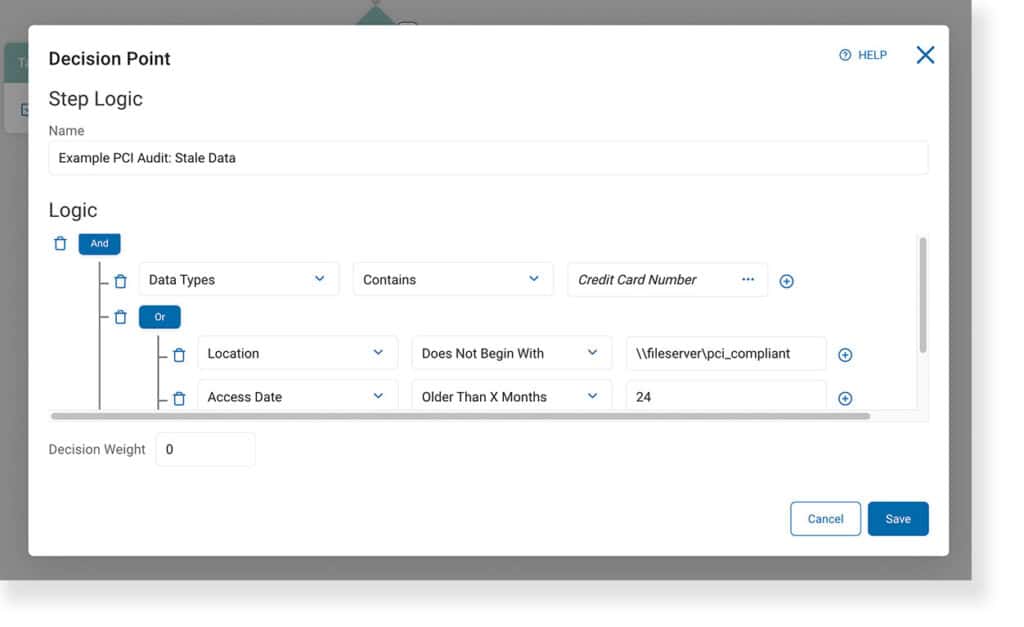
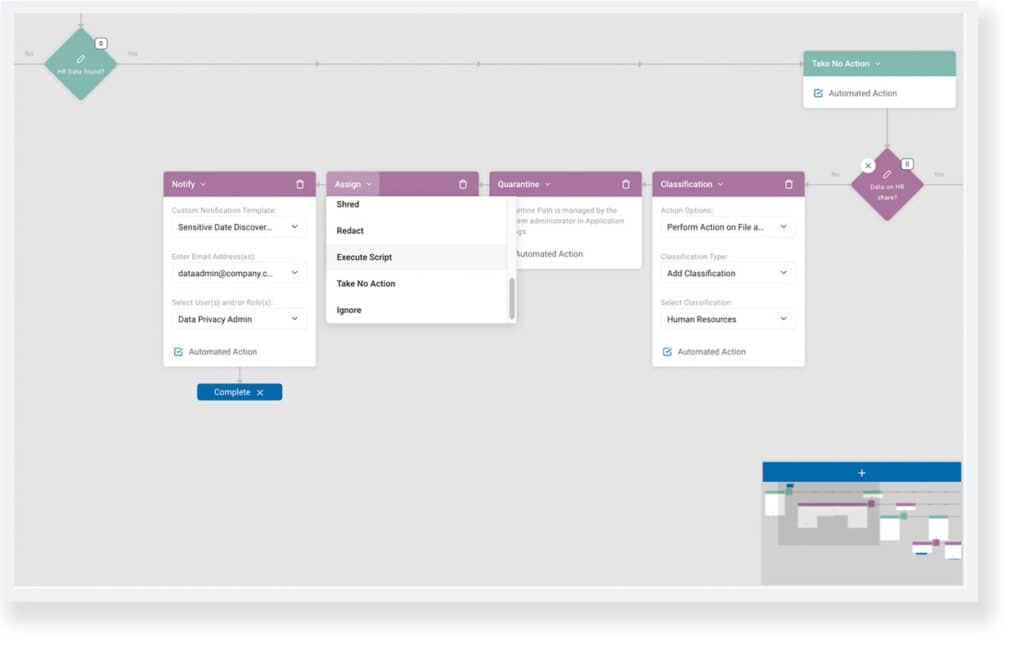
Spirion’s Playbooks are comprised of decisions that branch into sequences of (optionally automated) actions. Decisions themselves are specified by logical triggers that can assess both the content and context of a location targeted in a discovery scan. These workflows, defined in the Sensitive Data Platform (SDP) console, reflect an organization’s legal, regulatory, and contractual requirements (GV.OC-03).
The flexibility of playbook logic leads to the consistent enforcement of cybersecurity policies tasked with sensitive data risk management (GV.PO-01), executed through searches that yield quantifiable results (GV.RM-06). SDP delivers Privacy-Grade™ accuracy – across workstations, cloud storage, databases, and more – allowing organizations to operationalize their strategic direction though specific criteria (GV.RM-04).
Identify: Know the Unknown Unknowns
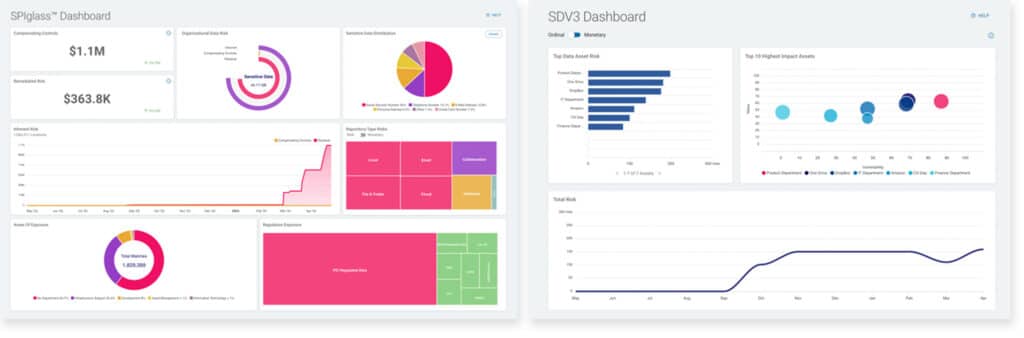
With a built-in Data Asset Inventory (DAI), SDP is designed to create a manifest of infrastructure hosting sensitive data (ID.AM-01). Assets can then be prioritized based on classification, criticality, resources, and impact determined by the insight of ongoing discovery scans (ID.AM-05/07) to make sure that they are intentionally managed throughout their life cycles (ID.AM-08).
The console’s SPIglass® and SDV3™ dashboards are informed by SDP’s DAI. These visualizations allow for risk responses to be properly prioritized (ID.RA-06) as vulnerabilities in assets are identified, validated, and recorded as match results (ID.RA-01). Once discovered, risk quantified through Spirion dashboards will guide improvements to DSPM policy with accurate data (ID.IM-01/03).
Protect: Tag, Data’s It
Persistent classification is an essential mechanism for safeguarding information against cybersecurity risks. SDP uses context-rich classification in addition to its direct integration with Microsoft Purview Information Protection to apply actionable orchestration hooks that optimize rights-management and DLP controls (PR.AA-05).
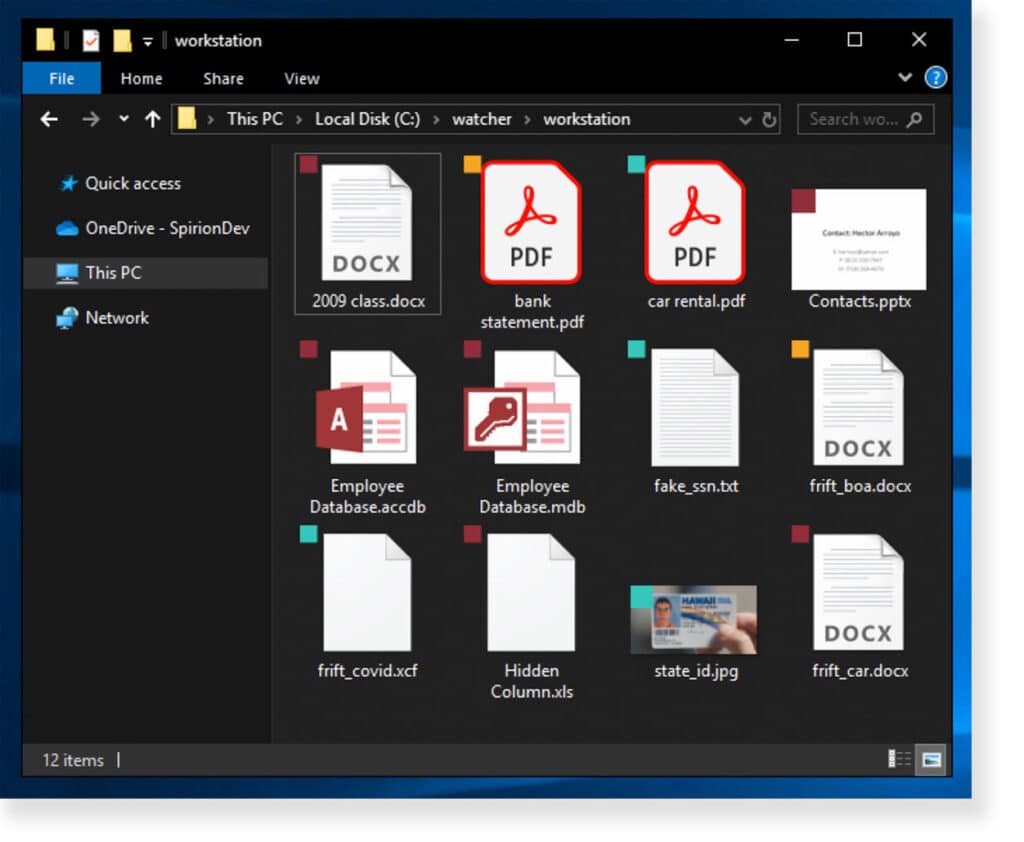
Spirion’s labels can also be overlayed as an icon directly visible to end users when they browse files, encouraging responsible awareness via easily recognizable, color-coded visual aids (PR.AT-01/02). By centralizing how classification taxonomies are enforced, as an outcome of discovery scans, sensitive data is managed consistently whether at-rest, in-transit, or in-use (PR.DS-01/02/10).
Detect: Don’t Fret
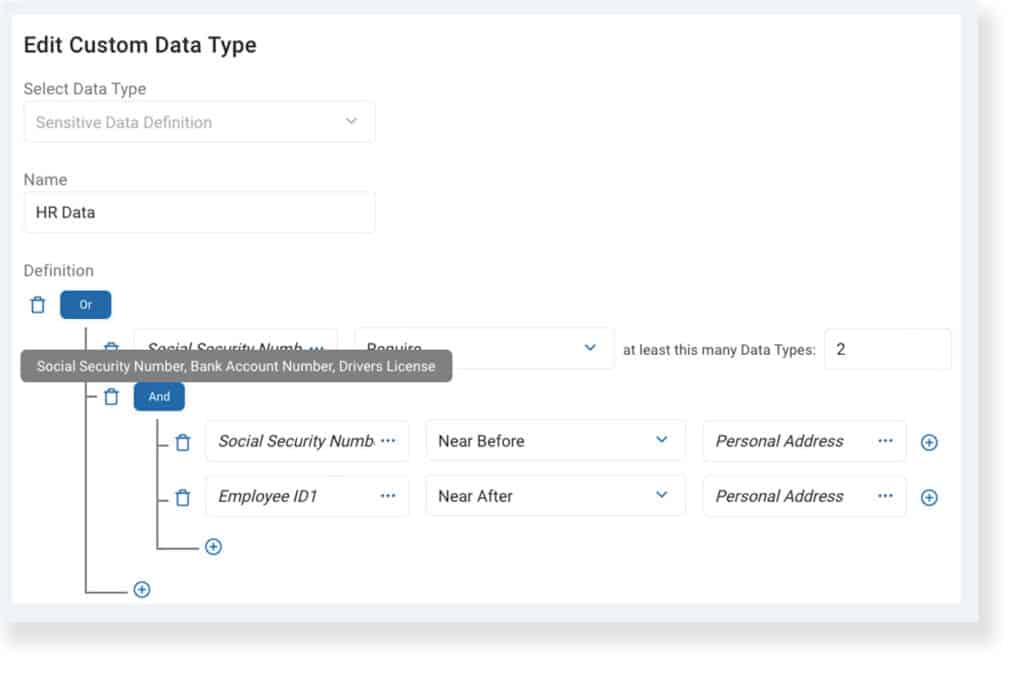
Data discovery is inherently an exercise in detection. Between its out-of-box AnyFinds™ and the customizable Sensitive Data Engine™, Spirion’s 98.5% accuracy rating means sensitive information is reliably monitored (DE.CM-09). Compound data types are built using parameters that support contextual verification to scan either file content or metadata, with the ability to set thresholds to establish match/incident criteria (DE.AE-07/08).
Sensitive Data Watcher, an additional offering in the Spirion Governance Suite, incorporates active data protection into SDP by monitoring file and folder activity on end-user workstations (DE.CM-03). By default, it looks for signs of compromise as designated by the MITRE ATT&CK® framework, and it can be further customized to detect events such as accessing classified information (DE.AE-02).
Respond: Incidents Happen
Playbooks, as mentioned previously, have two components: decisions & actions. The former was discussed regarding how decision logic reflects an organization’s governance strategy (RS.MA-03), while the latter drives Spirion’s capacity to (optionally) automate incident responses when sensitive data is detected (RS.MA-01/05).
Remediation is the only appropriate reaction to discovering that information repositories have exceeded the tolerable level of risk (RS.MA-02). SDP performs native as well as extensible actions – including dynamic script execution, templated notifications (RS.CO-02/03), and mitigation measures like being able to quarantine, redact, or shred offending match locations (RS.MI-01/02).
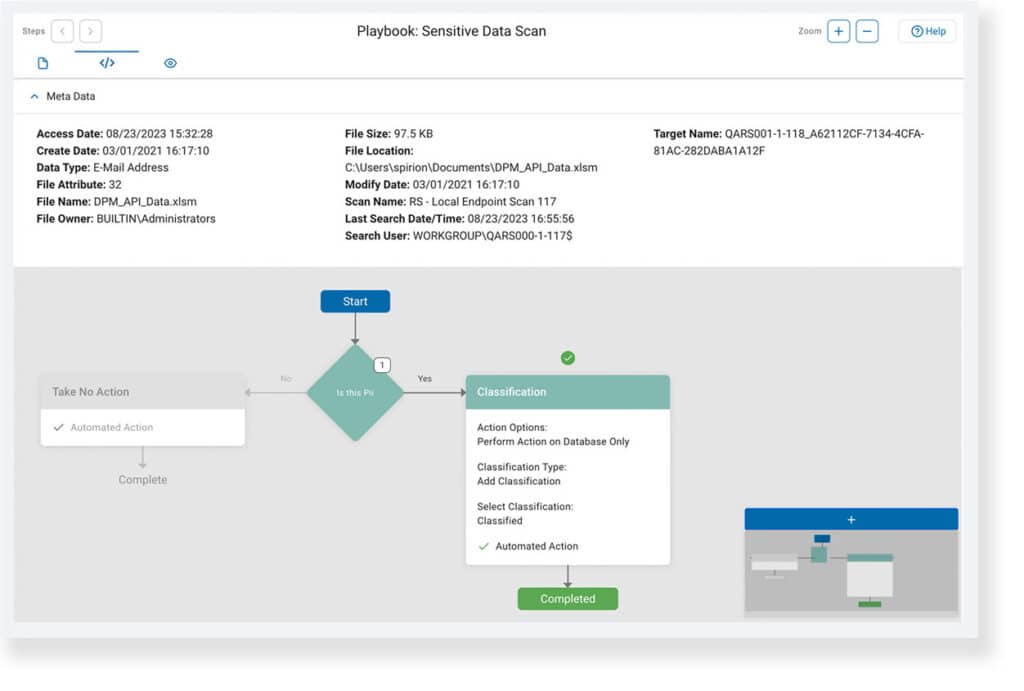
After a discovery scan has completed, a playbook executor view traces the response taken for every evaluated location (RS.AN-03/06). A contextual preview of the match itself is available for validation, if desired, and metadata for the match location is readily accessible (RS.AN-07/08).
Recover: Fail to Plan, Plan to Fail
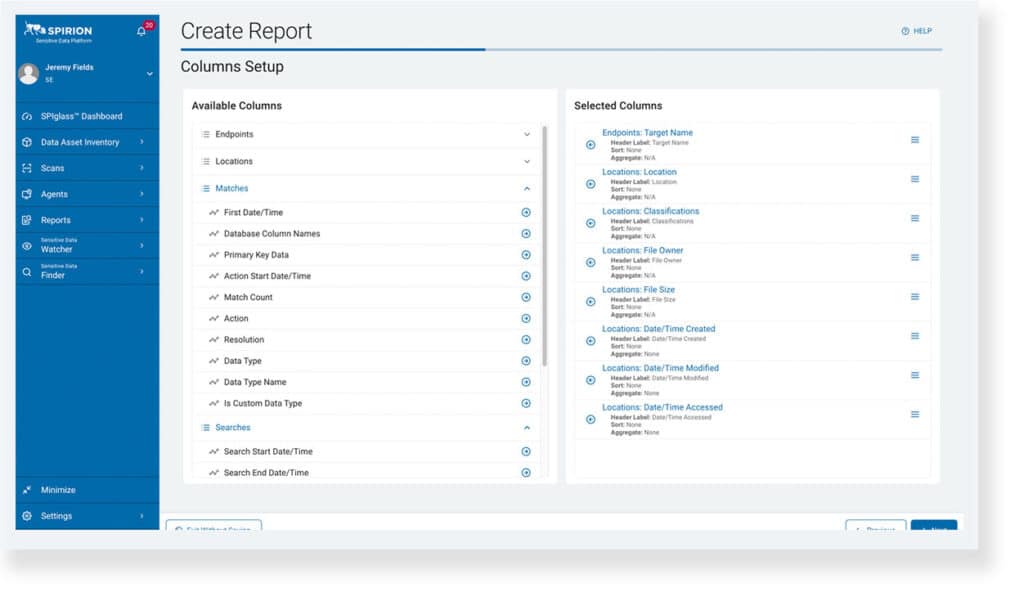
Lastly, Spirion’s reporting capabilities can help reconcile recovery efforts after incidents involving sensitive data occur since engaging in discovery scans inevitably produces a living record of locations containing critical information, which can be consolidated into custom reports that assist with scoping and prioritization (RC.RP-02).
Spirion data is exported through 2 formats: by using in-application custom reports or by externalizing the flow of information via Spirion Enhanced Analytics (SEA). In either scenario, reports on detection and response activities should be referenced to confirm the integrity and sensitivity of restored locations (RC.RP-03).
Quilty as Charged
If cybersecurity is a patchwork of concerns and solutions, NIST’s CSF is the thread that quilts it all together. Adhering to the framework is a commitment to continuous evaluation and improvement, making sure that success is achievable and auditable no matter the task at hand. The latest update, CSF 2.0, addresses many of the limitations that might have hindered its adoption in the past.
Data Security Posture Management initiatives greatly benefit from being organized around the proven methodologies outlined by NIST and summarized in this blog post. Spirion’s accurate discovery, automated classification, and actionable results lead to meaningful mitigation and reporting that scale as data footprints grow. Mapping key capabilities of Sensitive Data Platform to the 6 core functions of CSF 2.0 lays the groundwork for both formalizing organizational policy and efficiently centralizing data governance controls.